

Rs 6480 only/-
9907385555 asingh039@gmail.com
MP NAGAR BHOPAL
INTRODUCTION
As web is developing definitely clients are draw in by different specialist organizations step by step. Some of online shops, computerized showcasing, informal organization and so on. This simple access prompt change the proprietorship effectively, as clients can stolen other work and make computerized print with there name. In any case, this innovation offer ascent to new issue of piracy.
To conquer this issue numerous approaches were recommended and restrictive of the advanced information is protected. So to defeat this distinctive strategies are use for safeguarding the restrictive of the proprietor. Out of many methodologies advanced information inserting which is otherwise called computerized Data Hiding assumes a critical part. Keeping in mind the end goal to give proprietorship of the information proprietor, advanced information was implanted into the image, video, or information
Proposed Methodology
Main focus of this work was to cover up digital information in the picture. Entire work was done in two stages of hiding digital information and extraction of digital information. Here it is wanted that while extraction of secret information, [7, 8] whole data remain secured. In Fig. 3 entire inserting work piece graph is clarified.
CONCLUSION
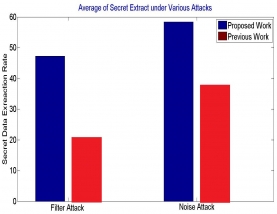
Here proposed work has efficiently hide data in the carrier image while security of the carrier is also maintained by embedding data in LL part of the image. Embedding is done by using histogram shifting algorithm where pixel value are shuffle as per the secret data. Proposed algorithm will recover or reverse complete data at receiver end, with carrier image in ideal condition. Results shows that the proposed work is producing the values which maintain the image quality as well as robustness. In future, work can be improve for other attacks such as geometry of image.
| IEEE Base paper | |||
| Doc | Complete Project word file document | ||
| Source Code | Complete Code files |