

Rs 5670 only/-
9907385555 asingh039@gmail.com
MP NAGAR BHOPAL
Digital Social community have moved toward becoming piece of our regular day to day existence. It is presently typical that individuals have accounts in numerous Social communities, sharing their considerations, advancing their work and most likely impacting a piece of the populace by means of them [1, 7]. An assortment of functionalities are given by these administrations, for example, video and photograph transferring, posting, informing, republishing and so on, contrasting as indicated by the stage and its point. Persuaded by the need to check the legitimacy and reliability of data that shows up on Social organizations, the nearness of people in various systems can be demonstrated especially valuable. Open data from one system can be utilized to approve the wellspring of data in another system. To accomplish this objective, there is a requirement for user recognizable proof crosswise over Social communities.
Whole work is divide into different modules base on the steps of calculation from the user query to final output. First include clustering of social user dataset by using genetic algorithm. Then in second phase by utilizing the cluster center from the cluster identification of similar user in other social network was done.
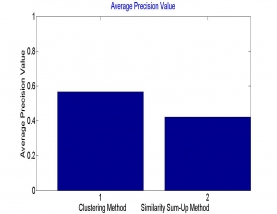
Connecting user identities across social media sites is not a straightforward task. The primary obstacle is that connectivity among user identities across different sites is often unavailable. In this work users are clustered into the respective group as per the feature similarity. Here three basic features are used which are common in inter network such as profile detail, content, etc. Here some of confusing features are escape from the dataset. Clustering of user dataset by an genetic approach has make an efficient cluster for making an effective retrieval. Here it is demonstrated that utilization of single element reduces the accuracy of the work, so multiple feature can increase the accuracy as done in this work. In future one can opt other feature combination with encryption for data security as well.
| IEEE Base paper | |||
| Doc | Complete Project word file document | ||
| Read me | Complete read me text file | ||
| Source Code | Complete Code files |