

Rs 7290 only/-
9907385555 asingh039@gmail.com
MP NAGAR BHOPAL
In digital watermarking inserting a message is done by hiding the digital media. This verify by the host or the owner or the composer of media. Recently various algorithms have been suggested for the watermarking video, video and audio. Currently the watermarking-algorithms asserted watermark in the spatial, frequency domains or wavelet domains. a number of algorithms use information as of multiple domains to embed the watermark. But what is the usefulness of watermarks in the varying domains.
Introduction
This work focus on the watermarking method where watermark is hide in the video by the change in the pixel value. So whole process is divide into two steps first is embedding where water which may be a image or text can be hide into the carrier video. While in the next step Extraction is done where water mark is extract from the carrier image which is obtained after the embedding. Here embedding steps are so taken that it can save the originality of the water mark from different attack.
Proposed method
Whole work is divide into two steps first is embedding where video frames are analyze and watermark bits are embedded into the frames while in next step watermark bits are extract from the embedded video that is term as extraction. So figure 4.4 represent the various steps of embedding.
Conclusions
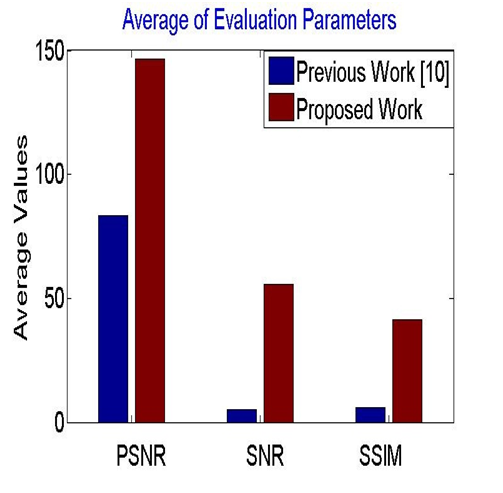
In this work, a new approach of watermarking is implemented where frequency domain is utilize for the work. Division of video in frames then in cubes lead to high efficiency of watermark embedding, so goal of invisible watermark get successful. Use of distance formula for the cube selection criteria make it a robust algorithm against different attacks. Proposed work is evaluated on the different attacks at different level such as spatial and geometrical. Results show that proposed work well in all condition with various parameters. It has been obtain that in ideal condition extraction rate was 100% while in case of spatial type attack proposed work is much better as compare to previous methods. Information hiding in video has make low degradation in video quality which was shown in results. There is always work in research so the system need improvement in cropping attack and rotation attack as well.
| IEEE Base paper | |||
| Doc | Complete Project word file document | ||
| Source Code | Complete Code files |