

Rs 3240 only/-
9907385555 deepaktest.patel@gmail.com
MP NAGAR BHOPAL
Secure Data communication Using Fountain Codes in Noisy Network
The objective of watermarking multimedia is to prevent unauthorized copies from being distributed without the consent of the original owner. The invisible watermarking algorithm proposed should be robust to common watermark attacks. Such a watermarking algorithm can be applied to digital audio, video, or image files. Extracting the watermark from any of these three media unambiguously identifies the head (owner), thereby creating the counterfeit of the main digitized medium extra challenging. In this paper a new approach of watermarking is studied in detail. Based on human perception view, watermarking process is classified into two broad categories so here it make a invisible watermarking technique. Results show that the proposed work is producing the results which maintain the image quality as well as robustness against the various attacks. Watermark obtain from the extraction method is having 69% of originality which is quit impressive results for all the researchers. This combinational approach of self reconstruction and watermarking tends to solve two purpose of the system. In future one can embed video using same approach for saving resource utilization.
Generate Fractal Code
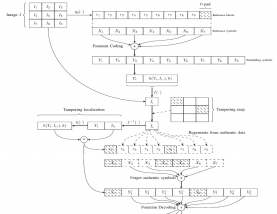
Different combination for block of image are pass into function in eq. 1 where n represent number of blocks to send in network, while m represent number of image block. Selection of block is depend on the matrix. Let us consider an image is divide into 60 blocks, then for each six block eight block are generate by fractal code.

Obtained fractal codes are send in network. It has been observed that for every six block of image corresponding eight block is generate by different combination of blocks using selection matrix X.
Receiver end work is shown in fig. 4 where reverse process is done.
Hash Value Checking
In this step blocks obtain from the network may get corrupt to check this hash value is generate from the block and check if this get corrupt then attach bits in fractal block is not same otherwise safe fractal block is receive.
Reconstruct Fractal Blocks
This step is for those fractal blocks whose hash value is same. So uninfected blocks are pass as per the inverse matrix of the selection matrix X. This give ouput of blocks which are same as done at sender end. So if few blocks get corrupt then due to presence of fractal codes image can be reconstruct at receiver end.
Matlab Projects With Source Code
| Doc | |||
| Source Code | Secure Data communication Using Fountain.ZIP |